搜索结果: 1-15 共查到“知识库 密码学”相关记录14074条 . 查询时间(2.843 秒)
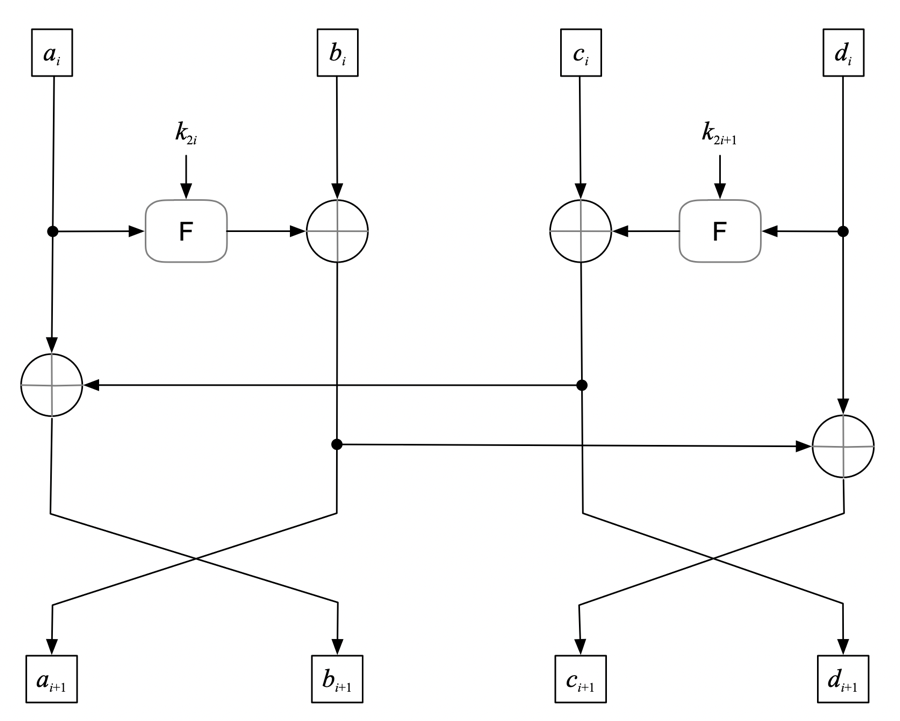
一种分组密码FBC的实现方法及装置(图)
分组密码 FBC 加密方法
2024/10/29
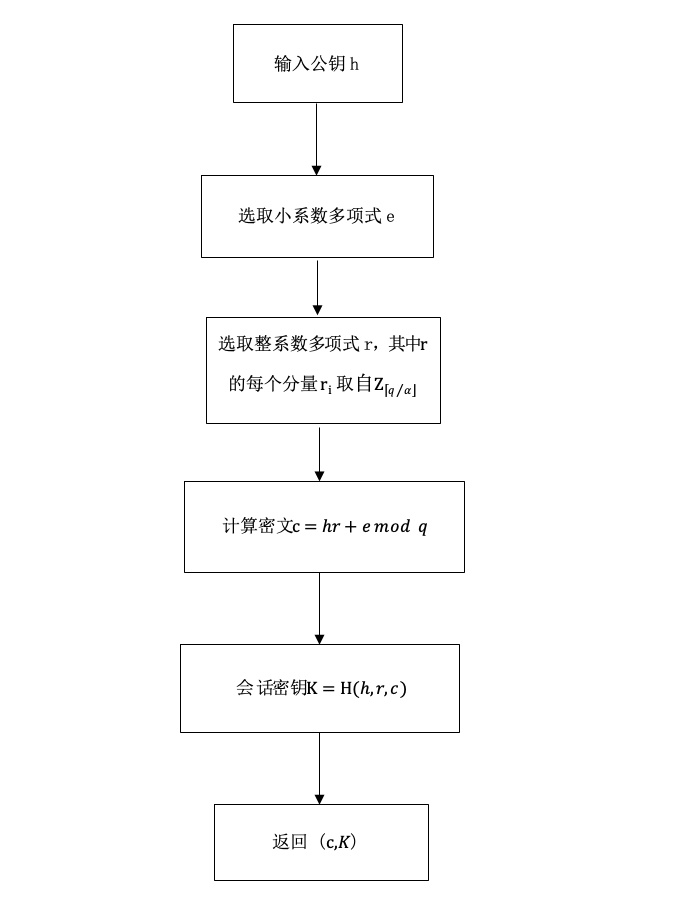
一种基于格的密钥封装方法(图)
基于格 密钥封装 信息安全
2024/10/29
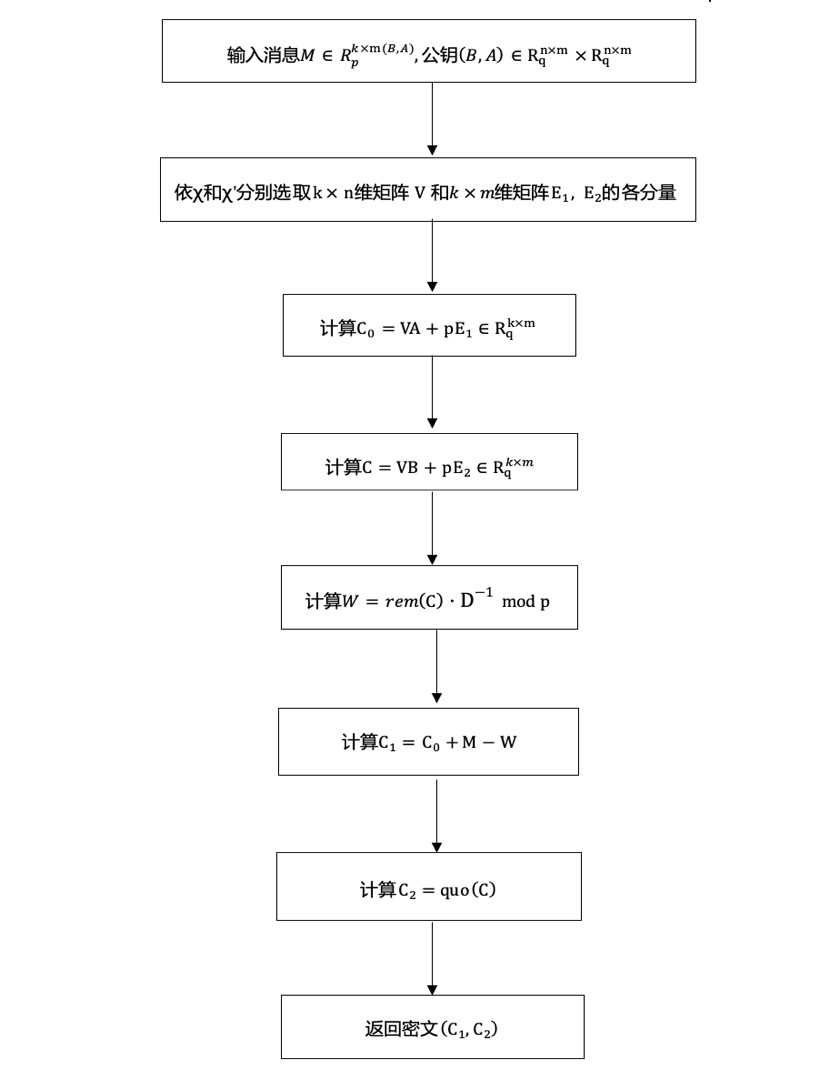
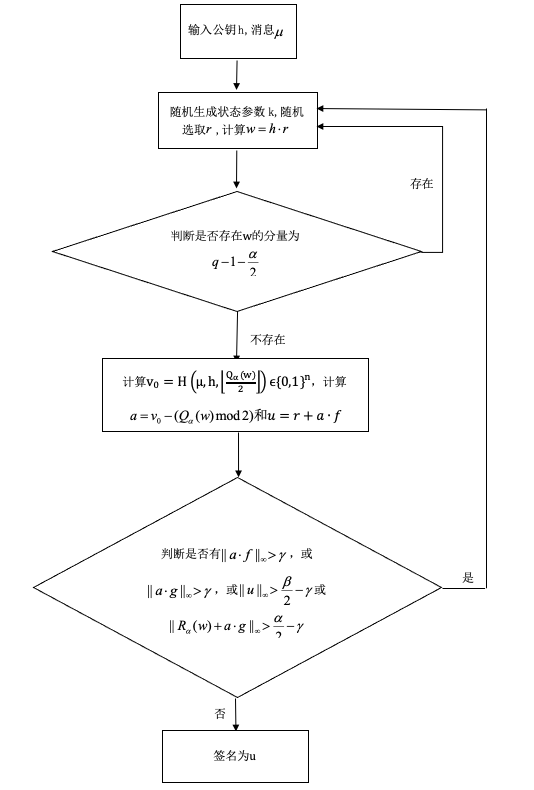
一种基于格的数字签名方法(图)
基于格 数字签名 公钥密码学 信息安全
2024/10/29
“打死我也不说”——数据加密技术(图)
数据加密 隐私 密电码
2023/11/6

《密码简史:穿越远古展望未来》(图)
密码 国家治理 现代化
2023/3/29
在人类的历史长河中,密码始终给人一种神秘的印象。在相当长的时期内,密码与政治和军事斗争密不可分,无论是在古代战场,还是在现代战争中,密码都扮演着重要的角色,是交战双方加密、破译、传递、获取情报的重要手段,也因此成为许多影视剧特别是谍战剧中的重要元素。在当前信息网络时代,密码被广泛地应用于政治、经济、社会各个方面,密码不仅是维护网络空间安全的重要法宝,也是构筑网络信息系统免疫体系和网络信任体系的基石...
Breaking and Fixing Anonymous Credentials for the Cloud (Full Version)
Attribute-based credentials Privacy-preserving authentication Strong authentication
2019/9/23
In an attribute-based credential (ABC) system, users obtain a digital certificate on their personal attributes, and can later prove possession of such a certificate in an unlinkable way, thereby selec...
Interactive oracle proofs (IOPs) are a hybrid between interactive proofs and PCPs. In an IOP the prover is allowed to interact with a verifier (like in an interactive proof) by sending relatively long...
A Framework for UC-Secure Commitments from Publicly Computable Smooth Projective Hashing
UC commitment smooth projective hash function SPHF
2019/9/23
Hash proof systems or smooth projective hash functions (SPHFs) have been proposed by Cramer and Shoup (Eurocrypt'02) and can be seen as special type of zero-knowledge proof system for a language. Whil...
Separating Standard and Asymmetric Password-Authenticated Key Exchange
PAKE Password-Authenticated Key Exchange
2019/9/23
Password-Authenticated Key Exchange (PAKE) is a method to establish cryptographic keys between two users sharing a low-entropy password. In its asymmetric version, one of the users acts as a server an...
Subversion-Resistant Commitment Schemes: Definitions and Constructions
Commitment schemes subversion security common reference string model
2019/9/23
A commitment scheme allows a committer to create a commitment to a secret value, and later may open and reveal the secret value in a verifiable manner. In the common reference string model, commitment...
With the burgeoning Vehicle-to-Everything (V2X) communication, security and privacy concerns are paramount. Such concerns are usually mitigated by combining cryptographic mechanisms with suitable key ...
Hardware-Software Co-Design Based Obfuscation of Hardware Accelerators
hardware security logic obfuscation hardware accelerator
2019/9/19
Existing logic obfuscation approaches aim to protect hardware design IPs from SAT attack by increasing query count and output corruptibility of a locked netlist. In this paper, we demonstrate the inef...
A Conditional Privacy Preserving Authentication and Multi Party Group Key Establishment Scheme for Real-Time Application in VANETs
Password Authentication VANET Group-Key generation
2019/9/19
Vehicular Ad-hoc Networks (VANETs) are a cardinal part of intelligent transportation system (ITS) which render various services in terms of traffic and transport management. The VANET is used to manag...


