搜索结果: 1-15 共查到“PUF”相关记录45条 . 查询时间(0.078 秒)
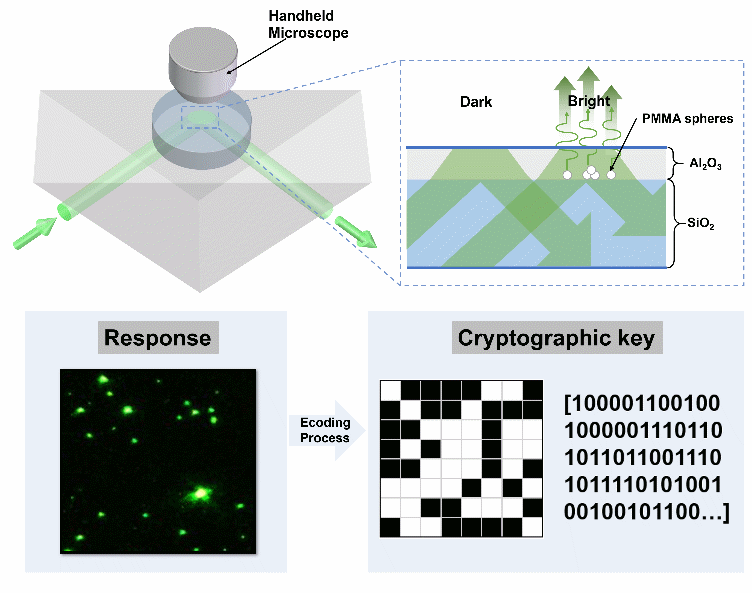
上海光机所提出了一种基于全内反射原理的高环境稳定性光学PUF的新方案(图)
反射原理 环境 光学
2024/8/15
2024年6月26日,中国科学院上海光学精密机械研究所高功率激光元件技术与工程部邵宇川研究员团队,提出一种基于全反射原理高环境稳定性光学PUF的新方案,相关研究成果以“Robust Optical Physical Unclonable Function Based on Total Internal Reflection for Portable Authentication”为题发表于ACS ...
Breaking the Lightweight Secure PUF: Understanding the Relation of Input Transformations and Machine Learning Resistance
Physically Unclonable Function Machine Learning Modelling Attack
2019/7/15
Physical Unclonable Functions (PUFs) and, in particular, XOR Arbiter PUFs have gained much research interest as an authentication mechanism for embedded systems. One of the biggest problems of (strong...
Deep Learning based Model Building Attacks on Arbiter PUF Compositions
physically unclonable function machine learning deep learning
2019/5/28
Robustness to modeling attacks is an important requirement for PUF circuits. Several reported Arbiter PUF com- positions have resisted modeling attacks. and often require huge computational resources ...
Physical Unclonable Functions (PUFs) have the potential to provide a higher level of security for key storage than traditional Non-Volatile Memory (NVM). However, the susceptibility of the PUF primiti...
Concealing Ketje: A Lightweight PUF-Based Privacy Preserving Authentication Protocol
Privacy-preserving authentication protocol Physically Unclonable Function Authenticated Encryption
2018/11/2
In this paper, we focus on the design of a novel authentication protocol that preserves the privacy of embedded devices. A Physically Unclonable Function (PUF) generates challenge-response pairs that ...
The Interpose PUF: Secure PUF Design against State-of-the-art Machine Learning Attacks
majority voting modeling attack propagation criterion
2018/4/20
Silicon Physically Unclonable Functions (PUFs) have been proposed as an emerging hardware security primitive in various applications such as device identification, authentication and cryptographic key...
Attacks on the PUF-Based Authentication Protocols YeHL16 and GaoMAAR17
PUF cryptographic protocols
2017/11/28
A physically unclonable function (PUF) is a circuit of which the input–output behavior is designed to be sensitive to the random variations of its manufacturing process. This building block hence faci...
MXPUF: Secure PUF Design against State-of-the-art Modeling Attacks
Arbiter physically unclonable function (APUF) modeling attack, propagation criterion reliability based modeling
2017/6/15
Silicon Physical Unclonable Functions (PUFs) have been proposed as an emerging hardware security primitive in various security applications such as device identification, authentication, and cryptogra...
Security Analysis of Arbiter PUF and Its Lightweight Compositions Under Predictability Test
PUF APUF
2017/5/27
Unpredictability is an important security property of Physically Unclonable Function (PUF) in the context of statistical attacks, where the correlation between challenge-response pairs is explicitly e...
PUF+IBE: Blending Physically Unclonable Functions with Identity Based Encryption for Authentication and Key Exchange in IoTs
Physically Unclonable Functions Identity based Encryption Internet of Things
2017/5/23
Physically Unclonable Functions (PUFs) promise to be a critical hardware primitive to provide unique identities to billions of connected devices in Internet of Things (IoTs). In traditional authentica...
TV-PUF : A Fast Lightweight Aging-Resistant Threshold Voltage PUF
Hardware Security Physical Unclonable Function (PUF)
2016/12/10
Physical Unclonable Function (PUF) is the hardware analog of a one-way function which can address hardware security issues such as device authentication, generating secret keys, producing seeds for Ra...
Distance Bounding (DB) is designed to mitigate relay attacks. This paper provides
a complete study of the DB protocol of Kleber et al. based on Physical Unclonable Functions
(PUFs). We contradict th...
Key Reconciliation Protocols for Error Correction of Silicon PUF Responses
physical unclonable function error correction key reconciliation
2016/12/8
Physical Unclonable Functions (PUFs) are promising primitives for lightweight integrated circuit authentication. Indeed, by extracting an identifier from random process variations, they allow each ins...
A Multiplexer based Arbiter PUF Composition with Enhanced Reliability and Security
Arbiter PUF (APUF) APUF compositions modeling attack
2016/12/7
Arbiter Physically Unclonable Function (APUF), while being relatively lightweight, is extremely vulnerable to modeling
attacks. Hence, various compositions of APUFs such as XOR APUF and Lightweight S...
Security features are of paramount importance for IoT, and implementations are challenging given the resource-constrained IoT set-up. We have developed a lightweight identity-based cryptosystem suitab...

